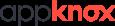
Cloud Security
Endpoint
Detection & Response.
Data Loss Prevention.
Privilege Identity/ Access Management.
Patch Management.
Insider Threat Detection.
Smart ID/ PKI/ SSO.
Enterprise Mobility Management.
Secure Enterprise Browser.
Data Privacy and Protection.
Remote Access Security.
Web Vulnerability Assessment. Integrated Vulnerability Management.
Vulnerability ManagementIT, OT, IoT.
Mobile Application Security.
Penetration Testing Software. Adversary Simulations.
Cloud Email Security.
DMARC Analyzer
DNS Security and Threat Protection.
Web Application Firewall. DDoS Protection.
External Attack
Surface Management.
Cloud Access
Security Broker.
Data Classification.
Managed File Transfer.
Digital Risk Protection. File & Folder Encryption.
Email Archival.
Encrypted USB Drives.
Security Configuration Management

Certificate Life Cycle Management.
Hardware Security Module/ Payment HSM.
Database Encryption and Masking.
Network Access Control.
Workspace Virtualization.
Multi-factor Authentication.
Network Monitoring and Mapping.
Service Desk. IT Asset Management.
Secure Remote Access.
Backup and IT Management Software.
Cybersecurity Training & Simulation Platform

Centralised Alerts and Notifications Management
Threat Exposure Management.
Operational Security
Mend.io

Navigating the New Frontiers of Cybersecurity
As cyber threats, technologies, and regulatory expectations evolve, Bulwark remains committed to guiding enterprises through this transformation with resilience, innovation, and trust, writes Jose Menacherry, Founder and MD of Bulwark Technologies
Breaking the Attack Chain
In this interview, Jenko Gaviglia, Director of Channel EMEA – Cybersecurity at Fortra, shares how the company’s “break the attack chain” strategy is helping organizations and partners stay ahead of evolving threats.
Breaking the Chain of Data Risk in MEA
Moe Bux, Channel Account Manager – Fortra, discusses how the company is helping organizations across the Middle East & Africa break the chain of data risk by integrating security, compliance, and partner-led execution into a unified approach.
Runtime security in focus
Noel Slane, Senior Director of Enterprise & Channel Sales at Invicti, explains why runtime security and proof-based scanning are reshaping how enterprises tackle application vulnerabilities.
Fixing AI risks at speed
AI is writing code and powering apps. Security must be designed for this new reality fast, developerfirst, and policystrong says Luis Bretones, Channel Director, EMEA & APAC, Mend.io in this interview.
Operational Excellence Driving Cybersecurity Evolution
Jessy Jose, Director of operations at Bulwark Technologies highlights how Bulwark’s success is built on a carefully curated, well-balanced cybersecurity portfolio that addresses every layer of defense
Securing Access and Boosting Response
JS Wong, CEO of Sendquick discusses how SendQuick’s MFA and AI-infused IT alerts build stronger cyber defences
Accelerating Cyber Resilience
Bulwark’s cybersecurity ecosystem empowers enterprises to stay ahead of next-generation threats, anchored by 25 years of trust, resilience, and innovation.
Zero Trust & Identity Security – Moving Beyond Traditional Security Paradigms
Instead of assuming that what’s inside the network is safe, Zero Trust continuously verifies every request, user, and device, regardless of location writes Murali Vellat,Division Manager, Bulwark Technologies
AI-Powered Mobile Security to the Forefront
Subho Halder, CEO & Co-Founder, Appknox outlines the company’s latest innovations, its strategy for the Middle East, and the trends that will define the next era of mobile application security.
Snapshots from Cybershield 2025
Vendor & Partner Testimonials
The Cyber Shift: intelligence, AI, and the Cloud Experts from Bulwark Technologies share their insights on key trends shaping the region, from threat intelligence and AI-powered SOC operations to the growing role of AI in marketing and the challenges of securing multi-cloud environments
The Shield Crossword Challenge


Over the past 25 years, cybersecurity has transformed from simple firewalls and antivirus tools into a vast ecosystem of advanced platforms, AI-driven defense, and compliance frameworks. Since 1999, Bulwark has stood alongside our vendors, partners, and customers, building resilience and digital trust across the region through every stage of this evolution.
Today, cybersecurity is no longer a technical afterthought; it is a boardroom priority, a business enabler, and a pillar of national security.
As organizations go through fast-paced digitalization, the protection of personal and sensitive information becomes paramount. Regulatory frameworks such as NESA, NCA, SAMA, PDPL, GDPR, and upcoming AI governance laws are reshaping how enterprises handle data.
Privacy is no longer just about compliance — it is about trust. Customers, partners, and regulators all expect transparency, accountability, and secure handling of data. AI introduces new complexities like training data, leakage to unintended exposure of sensitive information through AI models. Building privacy by design into every system is now a business imperative.
AI: The Double-Edged Sword
AI agents are rapidly becoming a part of our everyday reality. From virtual assistants managing business workflows to autonomous AI agents conducting research, drafting legal documents,
Navigating the New Frontiers of Cybersecurity
running cybersecurity scans etc, these digital entities are woven into applications, enterprises, and personal routines.
At the same time, malicious actors are deploying AI to create deepfakes, spread disinformation, and automate phishing and malware generation. With these, AI agents may become both codefenders and potential risk vectors. Managing AI deployments securely — with identity frameworks, policies, and governance — will be critical.
Quantum Readiness: Preparing for the Next Disruption
Quantum computing, though still emerging, poses a major risk. Its power to break existing encryption could render today’s cryptographic safeguards obsolete. This creates a “harvest now, decrypt later” threat — where encrypted stolen data today could be unlocked in the quantum future. The journey to Post-Quantum Cryptography (PQC) may take years. Organizations must start now by mapping cryptographic assets, piloting PQC algorithms, and ensuring crypto-agility. Much like the Y2K transition, this migration requires foresight and urgency. Those who act early will protect their digital foundations for decades to come.
Platform Consolidation
Platform consolidation in cybersecurity eliminates silos created by disparate point solutions, enabling centralized visibility, analytics, and control. While platform consolidation offers efficiency and unified control, achieving it is challenging. The consolidated platforms may also lack the agility or depth to counter new threat vectors immediately. Emerging threats like AI-driven attacks, deepfakes, zero-day exploits, and supply chain compromises often demand specialized tools for rapid detection and mitigation. The ideal strategy combines a unified core platform for efficiency with targeted niche technologies for adaptability and advanced defense.
Continuous Threat Exposure Management (CTEM)
CTEM is emerging as a must-have solution. CTEM delivers a real-time, prioritized view of exposures, helping security professionals to remediate before attackers exploit gaps. It provides a broader enterprise-wide security approach that continuously evaluates and validates an organization’s exposure to threats across entire attack surface and assets. It helps to prioritize risks based on business impact and provides remediation roadmap based on exploitable attack paths.
Application Security Posture Management (ASPM)
ASPM has become indispensable as applications are now the top attack vector. ASPM is a framework and set of tools designed to manage, monitor, and improve the security posture of applications across their lifecycle. It ensures that vulnerabilities, misconfigurations, and insecure practices in software development and deployment are identified and remediated continuously. Modern businesses rely on various application security tools — SAST, DAST, SCA, API, container, IaC. ASPM unifies these insights, eliminates noise, and provides CISOs with a single pane of glass into application risk.
Human Risk Factor
Human Risk Factor remains the weakest link in cybersecurity. Most breaches start from the human error, negligence, or manipulation. Empowering employees with knowledge and fostering vigilance transforms the human factor from vulnerability into an organizations strongest defense.
Looking Ahead
At Bulwark, as we celebrate 25 years of cybersecurity excellence, we are committed to bring the latest technology solutions – whether it is AI Agents Security, Post Quantum Cryptography readiness, Human Risk factor, CTEM or ASPM, we have the right solutions to address such requirements of our customers. We remain committed to our vendors, partners, and customers with the right technologies, insights, and expertise. Together, we can turn disruption into opportunity and build a safer, smarter digital future.
Let us step forward with clarity, confidence, and collaboration.
“Today, cybersecurity is no longer a technical afterthought; it is a boardroom priority, a business enabler, and a pillar of national security.”
Jose Menacherry Founder & MD
Bulwark Technologies
SHAPING A UNIFIED CYBER DEFENSE
In this interview, Jenko Gaviglia, Director of Channel EMEA – Cybersecurity at Fortra, shares how the company’s “break the attack chain” strategy is helping organizations and partners stay ahead of evolving threats.

Why is it important to break the attack chain?
Cyberattacks today are far more sophisticated than they used to be. We’re seeing attackers organize themselves into specialized teams—some focus on breaching the perimeter, others on extracting data, and still others on exploiting that information. This coordinated effort is what we refer to as the attack chain. The problem is, protecting just one part of that chain isn’t enough anymore. Organizations need security solutions that can disrupt the attack chain at multiple stages to effectively defend against modern threats.
How does Fortra’s portfolio specifically help organizations detect, contain, and neutralize threats at different stages of the attack lifecycle?
At Fortra, our portfolio is purpose-built to help organizations detect, contain, and neutralize threats across every stage of the attack chain. We’ve integrated a broad array of best-in-class cybersecurity solutions into a unified platform, enabling comprehensive protection from initial intrusion to data safeguarding and incident response. Our approach combines advanced threat intelligence, automation, and expert-driven tools to deliver full-spectrum visibility and control. For example, we help make infrastructure less vulnerable by identifying weaknesses and potential entry points
through our offensive security solutions. We also prevent attacks proactively using technologies like advanced web application firewalls (WAFs), secure gateways, and even user training programs designed to recognize and stop phishing attempts. When it comes to detection, our extended detection and response (XDR) capabilities, along with file integrity monitoring, allow organizations to identify malicious activity in real time. And even in the event of a successful breach, our data protection tools—such as data loss prevention (DLP) and file encryption—ensure that sensitive information remains secure and inaccessible to unauthorized actors. Ultimately, it’s the synergy of these solutions that sets Fortra apart. Each tool plays a critical role, but together they form a cohesive defense strategy that effectively disrupts the attack chain and empowers organizations to stay ahead of evolving threats.
How is Fortra enabling its channel partners to deliver this “break the attack chain” strategy effectively to customers?
Fortra is deeply committed to empowering its channel partners through the Fortra Protect Partner Program, which is designed to support a unified, end-to-end approach to cybersecurity. We recognize that our partners are an extension of our sales and strategic operations, so we’ve built a program that equips them with the tools, training, and resources needed to deliver comprehensive
solutions that disrupt the attack chain at every stage.
Through access to our full portfolio partners can offer integrated solutions rather than fragmented tools. This not only simplifies the customer experience but also strengthens the overall security posture.
We also provide tailored support across different partner types, whether they’re VADs, VARs, managed service providers, or strategic alliances. By enabling bundling, cross-selling, and recurring revenue opportunities, we help our partners grow their business while delivering real value to their customers. Ultimately, our goal is to make it easier for partners to articulate and implement a holistic cybersecurity strategy—one that truly breaks the attack chain and adapts to the evolving threat landscape.
Can you elaborate on how Fortra’s partnership with Bulwark enhances your regional reach and execution of this strategy in the Middle East?
Our partnership with Bulwark Technologies plays a pivotal role in extending Fortra’s cybersecurity vision across the Middle East. As an authorized value-added distributor, Bulwark brings deep regional expertise and a strong network of specialized system integrators and resellers. This allows us to deliver our “break the attack chain” strategy with precision and relevance to the unique
security challenges faced by organizations in the region.
Bulwark’s technical capabilities and commitment to customer success ensure that our solutions—ranging from data protection and secure file transfer to email security and offensive security—are implemented effectively and supported with the highest standards. Their presence across key markets, including the UAE and Saudi Arabia, enables rapid deployment, localized support, and tailored execution of our integrated cybersecurity offerings
What emerging attack techniques are you seeing in the EMEA region, and how is Fortra adapting its solutions to stay ahead?
The EMEA region is experiencing a surge in sophisticated cyber threats, many of which are being amplified by geopolitical tensions, evolving regulations, and the rapid adoption of AI technologies. We’re seeing increased use of AI-driven phishing, deepfake-enabled social engineering, and malware designed to evade traditional detection methods. To stay ahead of these threats, Fortra is continuously evolving its portfolio. We’ve enhanced our offensive security tools to proactively identify and remediate vulnerabilities before they’re exploited. Our threat detection capabilities—such as XDR and file integrity monitoring—are being refined to recognize more subtle and evasive attack patterns. We’re also investing heavily in data protection technologies like DLP and encryption to ensure that even if an attack succeeds, sensitive information remains secure. Moreover, we’re integrating AI and machine learning across our platform to improve threat correlation, automate response, and reduce the burden on security teams. This allows our customers in EMEA to respond faster and more effectively, even in complex and high-pressure environments.
Discuss highlights of your channel focus and channel enablement initiatives?
We’ve recently undertaken a comprehensive redesign of our channel program to better equip our partners for success. A key part of this initiative is the launch of the Fortra Academy, a centralized training hub where partners can access structured learning paths across our entire product portfolio.
This ensures they gain deep technical and functional knowledge of our solutions.
In addition, we’ve introduced a hands-on training program led by certified Fortra instructors. This initiative is designed to help partners not only understand our technologies but also confidently present, demonstrate, and implement them in real-world customer environments. It’s about empowering our partners with the skills and support they need to deliver value from day one.
By investing in education and enablement, we’re strengthening our partner ecosystem and ensuring consistent, high-quality execution of our cybersecurity strategy across all markets.
Discuss the focus on AI in your solutions?
AI and machine learning are central to how we help organizations in EMEA stay ahead of threats. By automating threat correlation across endpoints, networks, and user behavior, we can detect subtle attack patterns in real time.
This not only improves accuracy but also eases the workload on security teams, allowing them to focus on strategic tasks rather than manual triage. In fast-paced, high-risk environments, that speed and efficiency
make a critical difference
What would your key message to CISOs for the year ahead?
The attack surface is expanding at an unprecedented pace, and threat actors are becoming increasingly sophisticated. We’re seeing a rise in the volume and complexity of attacks, longer dwell times where adversaries remain undetected, and significantly higher costs for the targeted organizations.
In this environment, CISOs must take a holistic approach to cybersecurity—organizing their defenses across every link in the attack chain. That means minimizing vulnerabilities, deploying advanced prevention tools, training users to recognize and respond to threats, detecting malicious activity in real time, and protecting critical data to reduce impact.
Equally important is the need to continuously validate defenses, align security strategies with business objectives, and empower teams through automation and actionable intelligence. Security today is no longer just about prevention—it’s about adaptability, speed, and measurable outcomes. The organizations that will thrive are those led by CISOs who bring clarity, agility, and a proactive mindset to the forefront of their security strategy.
“We’ve integrated a broad array of best-in-class cybersecurity solutions into a unified platform, enabling comprehensive protection from initial intrusion to data safeguarding and incident response. Our approach combines advanced threat intelligence, automation, and expert-driven tools to deliver full-spectrum visibility and control.”
BREAKING THE CHAIN OF DATA RISK IN MEA
Moe Bux, Channel Account Manager – Fortra, discusses how the company is helping organizations across the Middle East & Africa break the chain of data risk by integrating security, compliance, and partner-led execution into a unified approach.
Digital transformation in MEA is creating both opportunity and risk. Why is “breaking the chain” so critical for organizations in this environment?
In the Middle East & Africa, businesses are advancing digital transformation at a pace the world is watching. But with opportunity comes risk. Every data leak, insider mistake, or phishing email has the potential to set off a chain reaction—from reputational damage to regulatory fines and loss of trust.
At Fortra, our mission is simple: Break the Chain. By working with partners across MEA, we help organizations disrupt threats before they spread, protect data before it’s exposed, and ensure compliance before regulators come knocking.
How does Fortra approach data protection differently?
Instead of siloed, reactive tools, Fortra delivers a connected ecosystem—from data classification and data loss prevention to digital risk protection and threat intelligence. This integration helps businesses break the chain at multiple points, making it harder for threats to escalate.
What data security challenges are most urgent for MEA?
The stakes in the region are high. Organizations face:
• National regulations like PDPL in Saudi Arabia and NESA in the UAE.
• Hybrid work risks, where employees move sensitive data beyond secure perimeters.
• Critical infrastructure threats, particularly in telecom, energy, and government.
• Sophisticated cybercrime campaigns targeting financial and retail sectors
• Each challenge represents a potential chain reaction—unless broken early.
How do Fortra’s solutions enable compliance?
Fortra makes compliance a natural outcome, not a painful process.
• Data classification tags sensitive data at the source, ensuring proper handling.
• DLP policies stop unauthorized transfers before breaches occur.
• Compliance reporting simplifies audits, reducing time and costs.
• By automating controls, Fortra enables organizations to break the compliance burden chain—turning it into a framework for resilience.
How does Fortra stay ahead of emerging threats?
Threats evolve, but so do we. Fortra combines global R&D, local threat intelligence, and alliances with cybersecurity councils to anticipate what’s next. This ensures that MEA organizations can break the attack chain at its earliest stage, before adversaries gain momentum.
What role do partners play in breaking the chain?
In MEA, our partners are the catalysts. They bring local knowledge, cultural insight, and trusted relationships that extend Fortra’s value. With our partners, we ensure that organizations not only adopt best-in-class solutions but also adapt them to regional realities—from regulatory compliance to language localization.

How does Fortra support its partners/ resellers?
Fortra is a partner-first company. We help the channel break the chain of go-to-market barriers by providing:
• Tailored training and certifications for technical and sales teams.
• Joint GTM campaigns that accelerate demand creation.
• Pre-sales, POCs, and co-delivery models to close deals faster.
• Dedicated partner success programs that drive long-term profitability
What’s next for Fortra in MEA?
The future is about smarter, faster, and AIdriven data protection. Fortra is expanding investments in:
• AI and automation to predict and prevent risks.
• Cloud-native security that scales with digital transformation.
• Partner ecosystem growth, ensuring more customers across MEA can break their risk chains.
At Fortra, “Break the Chain” is more than a slogan—it’s a movement. Together with our partners, we are breaking the chain of risk, compliance challenges, and cyber threats—so MEA businesses can innovate with confidence.
RUNTIME SECURITY IN FOCUS
Noel Slane, Senior Director of Enterprise & Channel Sales at Invicti, explains why runtime security and proof-based scanning are reshaping how enterprises tackle application vulnerabilities.
Let’s start with the basics. Why do you emphasize runtime in your messaging: “Attackers operate in runtime. Your AppSec should, too”?
It’s simple: vulnerabilities don’t exist in theory, they exist in reality—inside the applications that are running in production or pre-production environments. Attackers don’t look at static code repositories or pipeline configurations; they look for live weaknesses they can exploit.
Traditional security practices often emphasize pre-runtime checks, like static analysis, but these approaches can only tell part of the story. They tend to generate a high volume of false positives, and they don’t always reveal whether an issue is actually exploitable in the real world.
By focusing on runtime testing, Invicti’s DAST solutions emulate the behavior of attackers— crawling and probing applications in the same way an adversary would. This approach ensures that vulnerabilities are not only detected but also confirmed as exploitable. That’s a massive difference. It allows organizations to focus on real risks rather than drowning in unverified alerts.
Runtime testing aligns your defenses with the way attackers operate. In essence, we’re fighting fire with fire—testing applications in the same conditions under which they would be attacked.
How does Invicti DAST stand out compared to traditional scanning tools?
The advantages of Invicti DAST lie in three main areas: accuracy, scalability, and integration.
1. Accuracy through Proof-Based Scanning
Invicti pioneered the concept of proof-based scanning. Instead of simply flagging a possible vulnerability, the system safely exploits it in a controlled way to generate tangible evidence. For example, if it finds a SQL injection, Invicti’s scanner doesn’t just guess—it shows the actual query and result, proving the flaw exists. This drastically reduces false positives and gives developers confidence to fix the right issues.
2. Scalability for Enterprise Environments
Invicti’s solutions can scale to thousands of applications, both on-premises and in the
cloud. Enterprises often struggle with managing sprawling application portfolios. DAST allows security teams to continuously monitor applications without overwhelming resources, providing clear, prioritized insights.
3. Seamless Integration with DevSecOps
Application development today is fast-paced, and security needs to keep up. Invicti integrates directly into CI/CD pipelines, ticketing systems, and collaboration tools. That means vulnerabilities are automatically logged where developers work, ensuring issues can be fixed without slowing down innovation.
The end result is actionable security that doesn’t just check a compliance box—it enables organizations to genuinely reduce risk at scale.
How exactly does ASPM complement DAST? Think of it this way: DAST tells you which doors are open. ASPM tells you which doors matter most to lock.
DAST is excellent at confirming real, exploitable vulnerabilities in applications. But in large organizations, you’re rarely dealing with just one tool or one set of findings. You might have thousands of issues coming from multiple scanners.
ASPM complements this by:
• Aggregating results from multiple sources into a single pane of glass.
• Normalizing vulnerabilities so that “the same issue” reported by different tools doesn’t appear five times.
• Prioritizing based on business risk so teams know which vulnerabilities, if exploited, would impact mission-critical applications.
• Orchestrating remediation workflows by routing the right issue to the right developer with full context.
The combination of Invicti DAST and ASPM means organizations can go from identifying issues to systematically managing and remediating them across the enterprise.
Could you elaborate on the specific advantages organizations will see from Invicti

ASPM after the Kondukto integration? Certainly. Invicti ASPM, built on the foundation of Kondukto, offers several key advantages:
1 Unified Visibility – Instead of chasing alerts across multiple dashboards, teams get a centralized view of their entire application security posture.
2 Risk-Based Prioritization – Not every vulnerability is equally important. ASPM correlates vulnerabilities with business context—such as application criticality, data sensitivity, and exploitability—to focus on what truly matters.
3. Automation of Workflows – Security tasks can be automated, from assigning vulnerabilities to developers, to triggering re-scans after fixes. This reduces manual effort and accelerates response times.
4. Improved Collaboration – By integrating with ticketing systems like Jira or ServiceNow, Invicti ASPM ensures security and development teams speak the same language.
5. Continuous Compliance – With real-time visibility, organizations can more easily demonstrate compliance with regulatory frameworks like PCI DSS, HIPAA, and GDPR.
Ultimately, the advantage lies in moving from reactive firefighting to proactive management of application security risks.
The market is crowded with tools claiming to help reduce noise. How does Invicti’s ProofBased ASPM actually cut through the noise? This is a critical point. Security leaders often say their biggest challenge isn’t finding vulnerabilities—it’s figuring out which ones actually matter.
Invicti’s Proof-Based ASPM directly addresses this. By combining DAST’s proof-based scanning with ASPM’s orchestration capabilities, we can:
• Eliminate False Positives – If Invicti says a vulnerability exists, it’s backed by proof. This prevents wasted cycles chasing phantom issues.
• Provide Contextual Risk Insights – Proof-based results are enriched with business context in ASPM. For example, a SQL injection in a public-facing payment system is prioritized over a similar issue in a low-impact internal app.
• Streamline Remediation – Instead of flooding developers with noise, Proof-Based ASPM ensures only validated, high-impact vulnerabilities reach their workflow.
• Accelerate Time-to-Fix – Developers are more likely to act quickly when they’re confident an issue is real and critical.
This is what we mean by “cutting through the noise.” It’s about ensuring security and development teams are aligned, focusing their energy on the vulnerabilities that truly reduce
organizational risk.
Looking ahead, how do you see the future of application security evolving with these innovations?
The future of application security is about convergence and automation.
• Convergence: We’re moving away from siloed tools and toward unified platforms that bring together scanning, orchestration, and prioritization. Invicti’s combination of DAST and ASPM is a reflection of that trend.
• Automation: Manual triage and remediation simply can’t keep up with the pace of modern development. Automation, driven by accurate data, will be the cornerstone of AppSec

In Focus
Attackers operate in runtime. Your AppSec should, too. In the fast-paced world of modern software development, security teams are constantly struggling to keep up. Agile development, DevOps workflows, and continuous deployment have drastically shrunk release cycles, making it harder than ever to ensure every application and API is secure before it goes live. Attackers exploit vulnerabilities at runtime—when an application is fully deployed and operational. This is where Dynamic Application Security Testing (DAST) and Application Security Posture Management (ASPM), especially when anchored in proofbased validation, become essential to building a security program that operates at the speed of the business.
The Power of Proof-Based Scanning
The single most significant advantage of Invicti DAST is its patented Proof-Based Scanning technology
Eliminates False Positives: Invicti automatically and safely verifies the exploitability of over
programs.
• Shift-Right and Shift-Left Together: It’s not about choosing between early detection in pipelines (shift-left) or runtime testing (shift-right). It’s about embracing both, with proof-based results guiding decisions at every stage.
In short, application security will no longer be a bottleneck. With the right platforms, it will become a seamless part of the software lifecycle, empowering organizations to innovate securely.
Invicti Security’s vision is clear: by combining the accuracy of proof-based DAST with the orchestration power of ASPM, enterprises can finally cut through the noise, focus on real risks, and build a proactive AppSec posture.
%94 of direct-impact vulnerabilities (like SQL Injection and Cross-Site Scripting) with %99.98 certainty. This is done by generating a proofof-exploit, which shows the security team and developers exactly how the flaw can be exploited and, crucially, that it is a real issue.

Trust and Efficiency: By eliminating the noise of unverified findings, security teams no longer waste countless hours manually triaging alerts. Development teams receive tickets for issues that are confirmed and actionable on day one, dramatically accelerating the remediation process and fostering better collaboration
Comprehensive Coverage Invicti DAST is designed for the modern application landscape, covering:
• Web Applications and APIs: It scans everything from legacy applications to complex, dynamic SinglePage Applications (SPAs) and all major API
protocols, including REST, SOAP, and GraphQL.
• API Discovery: It automatically finds shadow APIs—endpoints that are not documented but are live and potentially exposing sensitive data—eliminating blind spots in your security posture.
• Shift-Left Integration: Despite being a runtime testing tool, modern DAST can be seamlessly integrated into CI/CD pipelines. This allows developers to get real-time, confirmed vulnerability feedback on early builds before issues become costly to fix in later stages.
Fixing AI risks at speed
AI is writing code and powering apps. Security must be designed for this new reality fast, developer-first, and policy-strong says Luis Bretones, Channel Director, EMEA & APAC, Mend.io

What are the biggest opportunities and risks AI introduces into enterprise security today?
Opportunities: AI amplifies security and engineering by automating checks at scale, accelerating triage, and proposing contextaware fixes in the IDE/PR—raising coverage without throttling delivery. It enables continuous assurance with guardrails as code is written and policies that autoenforce in CI/CD.
Risks: the same speed can spread insecure patterns (SSRF, injection, hardcoded secrets, outdated libraries); LLMs may hallucinate or bypass auth; and new surfaces emerge—prompt injection, jailbreaks, insecure output handling, model/ embedding leakage, over-privileged tools/
agents, and poisoned data. The AI supply chain demands an auditable AI-BOM and a stance of untrusted by default, backed by least-privilege tooling, secret/PII controls, policy-as-code for residency/licensing, redteaming, and continuous monitoring for drift and abuse.
How is Mend.io embedding AI to secure applications and software supply chains?
Mend.io runs where developers work and as code is created—integrating with popular IDEs, pull requests, and modern CI/CD—to deliver lightweight, real-time checks that stop issues before they leave a branch or pipeline. Findings are enriched with code and dependency context, and AI-powered remediation proposes safe, reviewable
diffs—complete with rationale developers can evaluate in the normal code-review flow. Unified coverage spans proprietary code (SAST), open source and licenses (SCA), containers and images, and the emerging layer of AI components (models, prompts, agents, datasets), tracked via an AI-BOM and governed by policy. A single policy engine drives risk-based prioritization, automated enforcement, and executiveready reporting across repos, services, and regions—preserving build velocity while raising the security baseline. In practice, security shifts from a late-stage gate to a continuous assist that lives inside the developer workflow and scales with the organization.
What makes Mend.io the first AI-native AppSec platform—and why is that essential in EMEA & APAC?
AI-native means securing software built with AI (generated code) and from AI (apps composed of models, prompts, agents, tools, and data flows). Practically, it’s (1) instant analysis and fixes at creation— IDE/PR checks tuned to LLM-introduced patterns, secret detection, and supply-chain vetting before code leaves a branch; (2) an AI-BOM with policy controls and behavior testing—prompt/agent hardening, leastprivilege tool use, red-teaming and safety tests, and data-loss protections across inputs/outputs/logs; and (3) AI-assisted prioritization and remediation—risk scoring that de-duplicates noise, explains root cause, and proposes reviewable patches with verification gates. It matters across EMEA/APAC because diverse data-residency and sectoral rules (e.g.,
GDPR/NIS2, PDPA variants), multilingual distributed teams, and partner-heavy supply chains demand consistent, localizable controls with auditability and per-tenant policy enforcement—delivered without sacrificing developer speed or platform performance.
How does Mend.io secure AIgenerated code and embedded AI agents? (AI Gen Code Security & AI App Security)
AI Gen Code Security: Inline, real-time SAST/ SCA tuned for LLM-introduced mistakes (unsanitized inputs, missing auth, weak crypto), plus secrets and unsafe libraries. Findings come with explainable fixes in IDE/ PRs, while CI runs deeper, policy-gated scans. Optional auto-remediation with approvals blocks risky changes and fasttracks safe patches.
AI App Security: Automatic discovery and an auditable AI-BOM for models, vector DBs, tools, datasets, prompts, and agents. Policy guardrails enforce licensing, data residency/
A CISO’s New Imperative
Artificial intelligence has shifted from a promising innovation to an operational backbone, powering everything from customer-facing chatbots to autonomous agents driving business workflows. Yet, while adoption has accelerated, security measures have lagged, leaving organizations exposed to emerging threats such as data leakage, model manipulation, supply chain compromise, and AI-driven misinformation. Large Language Models (LLMs) in particular introduce vulnerabilities beyond the reach of traditional AppSec tools, including prompt injection attacks, excessive decision-making
minimization, and least-privilege tool use, with prompt hardening and output filters. Continuous behavioral testing/red-teaming drives actionable remediation and runtime monitoring, with SIEM/SOAR integrations for visibility.
Mend SAST delivers realtime, AIpowered remediation in the developer workflow. How does this enable “shift left” without sacrificing safety?
Developers get nearinstant feedback while context is fresh; proposed patches are codereviewready diffs with rationale; and verification scans/tests guard quality before merge. Outcomes: fewer tickets, faster PRs, and a higher security baseline—without detours to standalone dashboards.
How does Mend.io unify risk across code, containers, and open source while maintaining speed and scale?
A single platform correlates SAST, SCA, and container/image signals under one policy engine and severity model. Consistent
governance, automated enforcement, and executive reporting provide a single source of truth. Native CI/CD and registry integrations preserve build velocity while scaling across repos, services, and regions.
How does Mend.io work with Bulwark Technologies and channel partners to drive adoption?
Through distributors and regional partners— such as Bulwark Technologies—Mend.io delivers localized enablement, training, and implementation support across the Middle East, Africa, and beyond. Comarketing and joint solutions help customers operationalize AInative AppSec quickly and sustainably.
What is the key takeaway with an AInative approach?
AI raises the bar for speed—and for safety. An AInative approach secures what AI creates and how AI behaves, unifying policy and remediation from the first line of code to production.
autonomy, and the inadvertent disclosure of sensitive information. These risks carry serious business consequences—data breaches, reputational harm, legal liability— and demand a shift in mindset: treating AI systems as untrusted components and embedding protection from the design phase onward.
From Risk Awareness to Action
Forward-thinking CISOs are now integrating AI-specific safeguards into threat modeling, governance, and incident response, aligning with frameworks such as the OWASP LLM Top 10. Proactive measures include secure coding practices for
AI workflows, rigorous supply chain vetting, and continuous monitoring for anomalies like unbounded consumption or unauthorized data access. Legal compliance is equally vital—ensuring license adherence, protecting data residency, and mitigating liability from harmful outputs. By adopting a “security by design” approach, assigning clear ownership for AI risk management, and embedding safeguards throughout the AI lifecycle, organizations can unlock AI’s transformative potential without opening the door to avoidable vulnerabilities. In the era where AI is both a competitive advantage and a potential attack surface, resilience isn’t optional—it’s the cost of doing business.
Operational Excellence Driving Cybersecurity Evolution
Jessy Jose, Director of operations at Bulwark Technologies highlights how Bulwark’s success is built on a carefully curated, well-balanced cybersecurity portfolio that addresses every layer of defense
As the cybersecurity landscape continues to evolve at an unprecedented pace, operational excellence and adaptability have become key differentiators in the value-added distribution ecosystem. At Bulwark, our operations are strategically aligned to empower partners, enable customers, and enhance the overall cybersecurity posture of the region.
For over two decades, Bulwark has been more than a distributor — we have been a cybersecurity enabler, bridging global technologies with regional expertise. Our operational framework is designed not only to drive efficiency but to ensure that every partner we work with is future-ready in a rapidly shifting threat environment.
Differentiation Through a Strong Portfolio and Deep Enablement
Bulwark’s success is built on a carefully curated, balanced cybersecurity portfolio that addresses every layer of defense — from network and endpoint protection to identity, data security, cloud protection, and compliance management. We partner only with best-of-breed, globally recognized vendors, ensuring our channel ecosystem delivers comprehensive, integrated, and modern security architectures.
But what truly differentiates Bulwark is not just the range of solutions we offer — it’s the depth of enablement we provide. Our operations team ensures every partner receives end-to-end support: from onboarding, technical training, and certification programs to pre-sales assistance and post-deployment guidance. This holistic approach transforms partners from sellers into trusted cybersecurity advisors.
Moving from Reactive to Proactive, Intelligence-Driven Security
Cybersecurity today is no longer about waiting for incidents — it’s about anticipating, analyzing, and acting before threats emerge. At Bulwark, we work closely with partners and customers to help them shift from reactive defense to proactive, intelligence-led cybersecurity.
Our model helps organizations gain visibility, context, and control — enabling them to detect, predict, and mitigate threats in real time.
Building a Go-to-Market-Ready Portfolio with Technology vendors
A key aspect of our operations is the close collaboration we maintain with technology vendors. We don’t just distribute products — we co-create market strategies. Our team works with each vendor to identify the right product-market fit, localize offerings for regional compliance, and bundle complementary solutions to deliver complete cybersecurity frameworks.
This synergy enables Bulwark to maintain a go-to-market-ready portfolio aligned with global innovation and local business realities.
Assessing Partner Readiness Before Introducing New Technologies
Before any new solution is introduced into our ecosystem, we conduct a comprehensive partner readiness assessment — evaluating technical competency, market reach, customer verticals, and service delivery capabilities.
Partners found suitable receive structured onboarding support, including:
• Product and sales enablement sessions
• Training and certifications for sales and technical teams
• Access to demo environments and proof-of-concept (POC) labs
• Co-marketing and lead-generation campaigns
This process ensures every new technology we bring to market is launched through well-prepared partners, driving successful adoption and steady revenue growth.
Education and Hands-On Technical Exposure: The Core of Engagement
At Bulwark, education is a continuous operational discipline. Our enablement programs, certification drives, and hands-on workshops give partners real-world exposure to emerging cybersecurity technologies.
Our lab environments and demo centers let partners experience solutions in action, strengthening their ability to position and implement technologies confidently. This focus on experiential learning and skill development remains central to our long-term partner engagement strategy.

The Growing Shift Toward Managed Security Services (MSS)
Across the region, we are witnessing a strong shift among our channel partners toward managed security service models. Many partners are transforming from traditional resellers into MSSPs, offering continuous protection, monitoring, and compliance services.
Bulwark plays a pivotal role in this transformation by:
• Supporting partners in building MSS frameworks and service portfolios.
• Providing access to cloud-native, subscription-based, licensing model that enable managed offerings.
• Assisting in operational alignment for recurring revenue generation and service-level delivery.
This evolution is enabling our partners to deliver sustained value, recurring business, and enhanced customer trust.
Operational Excellence as a Growth Catalyst
At Bulwark, operations is not merely about logistics or process - it’s about orchestrating value across the cybersecurity ecosystem. Our operational strategy revolves around one goal: to empower our partners with the right technologies, the right training, and the right tools to succeed in a dynamic market.
As we continue to grow our presence across the Middle East region and India, our focus remains clear — to maintain a resilient, proactive, and intelligence-driven channel ecosystem that protects organizations and powers progress in the digital era.


Acyber breach can occur in seconds, yet the repercussions can last for a long time. Even short periods of downtime can disrupt operations, unsettle customers and harm hard-earned reputations. Preventing this requires more than strong perimeter security. It demands clear visibility over who is accessing critical systems, and the ability to alert the right people as soon as a threat is spotted.
A key part of that defence is Multi-Factor Authentication (MFA), which requires multiple forms of verification beyond just passwords. But keeping attackers out is only half the battle. Organisations also need the speed and accuracy to respond when an incident or breach occurs. This is where an intelligent IT Alert system delivers value, working alongside cyber threat detection tools such as SIEM, to track suspicious activity in real time and notify the right stakeholders instantly.
SendQuick, a leader in enterprise messaging and MFA solutions, is addressing both challenges with its FIDO-2certified SendQuick Conexa, and AIinfused IT alerting capabilities, designed to help IT teams act faster and with greater precision.
Stronger Authentication with FIDO-2
Certified MFA
Passwords remain a common entry point for attackers, often compromised through phishing, credential stuffing or brute force attempts. Systems that rely solely on passwords are
Securing Access and Boosting Response:
JS Wong, CEO of Sendquick discusses how SendQuick’s MFA and AI-infused IT alerts build stronger cyber defences
increasingly vulnerable.
SendQuick Conexa is now certified under the FIDO2 standard by the FIDO Alliances, enabling passwordless authentication backed by strong cryptography. Sensitive data, such as passwords or one-time codes, is never stored or transmitted.
These are the key advantages for businesses with this upgrade:
• Stronger security with public key cryptography.
• Protection from phishing and credential reuse.
• Simple, passwordless login experiences using biometrics, hardware tokens or security keys.
• Broad compatibility with devices, browsers and platforms.
For highly regulated sectors such as finance, healthcare and government, this enables compliance while improving usability. It safeguards against account takeovers, secures remote access and supports audit readiness.
AI-Infused IT Alert and Notifications - Precision and Speed in Incident Response
In fast-moving IT environments, too many unfiltered alerts can overwhelm teams, delay action and cause critical issues to be overlooked. SendQuick’s AI-infused IT Alerts solution are designed to focus attention where it is needed most.
Key enhancements include:
• Alert Priority: Automatically ranks incidents based on severity and impact so critical issues receive immediate attention.
• Noise Reduction: Filters out unnecessary or duplicate alerts to prevent distraction
• Channel Failover: If one communication channel is unavailable, alerts automatically switch to the next available channel to guarantee delivery.
• Escalation: Routes unresolved or ignored alerts are escalated to higher-level responders, ensuring urgent matters are never left unattended.
• Policy Filter: Applies custom alert rules based on organisational priorities, security policies and operational requirements.
• Predictive with Machine Learning: Analyses patterns in system behaviour to forecast potential failures before they happen, enabling preventive action.
This combination of intelligent filtering, delivery assurance and predictive capability allows organisations to detect and act on threats or failures faster, reduce downtime and maintain uninterrupted services.
Why Organisations Choose SendQuick
By combining secure, passwordless MFA with AI-infused IT Alerts, SendQuick strengthens both prevention and response. This integrated approach reduces operational risk, improves service reliability and supports compliance requirements.
Customers benefit from:
• High security with minimal disruption to users.
• Reliable communications, even during network outages.
• Seamless integration with existing IT tools and workflows.
• Greater confidence that urgent alerts are delivered, acted upon and resolved.
Looking Ahead
Cybersecurity threats will continue to evolve, but the goal remains the same: protect systems, minimise risk and maintain business continuity.
SendQuick’s FIDO2 certified MFA and AI infused IT Alert and Notification solutions give organisations the tools to respond faster, prioritise effectively and operate with confidence.
With SendQuick, every second becomes an opportunity to protect operations, strengthen resilience and safeguard the future of your organisation.
For more information, visit www.sendquick.com, email info@sendquick.com, or scan the QR code on the adjacent page for a free demo.

Accelerating Cyber Resilience
Bulwark’s cybersecurity ecosystem empowers enterprises to stay ahead of next-generation threats, anchored by 25 years of trust, resilience, and innovation.
For a quarter of a century, Bulwark Technologies has stood as one of the region’s most enduring cybersecurity distributors, an organization that has consistently evolved alongside the industry’s most defining transformations. What began in 1999 as a modest venture offering niche security solutions has grown into a powerhouse representing over 30 globally trusted vendors across the Middle East, India, and Africa.
Through waves of technological disruption, from the rise of cloud computing to today’s AI-driven revolution, Bulwark has expanded and consolidated an extensive portfolio of cybersecurity solutions that address different requirements.
From Resilience to Reinvention
Over the years, Bulwark has proven its resilience through global economic
cycles, shifting IT priorities, and the evolving nature of cyber threats. In its early years, cybersecurity was often an afterthought in IT strategies. Today, it’s at the core of digital transformation, and Bulwark’s journey mirrors that evolution.
The company has built its reputation on enduring strategic partnerships rooted in trust, long-standing vendor alliances, and deep technical expertise that adapts to the region’s unique needs. Its ability to align cutting-edge technologies with local requirements such as compliance frameworks, hybrid infrastructure challenges, or emerging AI-driven risks has helped Bulwark steadily strengthen its credentials as both a strategic enabler and a trusted advisor.
As the digital landscape becomes increasingly complex, Bulwark continues

to focus on enabling enterprises to fix cyber risks at speed without compromising business agility or innovation. Bulwark’s approach is built around six core pillars that together provide a comprehensive and layered cybersecurity defense.
As the digital landscape becomes increasingly complex, Bulwark’s continues to focus on enabling enterprises to fix cyber risks at speed without compromising business agility or innovation.
Cloud Security
As workloads increasingly move to the cloud, resilience becomes paramount. Bulwark’s cloud security portfolio brings together cloud email security, DMARC analyzer, DNS security, web application firewall, DDoS protection, external attack surface management, and cloud access security broker solutions. The focus is on securing workloads, users, and data across multi-cloud and SaaS environments.
By enabling continuous visibility, control, and threat prevention, Bulwark helps enterprises strengthen cloud governance and safeguard digital assets against the expanding spectrum of cloud-borne risks. The vendors in this portfolio include Mimecast, DNSFilter, RiskProfiler, and Radware.
Data Security
As data continues to grow exponentially across hybrid and cloud environments, protecting information integrity and privacy has become a top enterprise priority. Bulwark offers a comprehensive portfolio of data security solutions from leading global technology vendors, which enable enterprises to safeguard their most critical data assets through a layered security approach. These solutions span data classification, managed file transfer, encryption, digital risk protection, and secure hardware-based encryption.
Combined with configuration management, database masking, and certificate lifecycle management, these capabilities ensure comprehensive protection, compliance, and resilience across on-premises, cloud, and hybrid infrastructures. Some of the key vendors in this portfolio include Fortra, Tripwire, Utimaco, CryptoBind, AppViewX, GoAnywhere, Resecurity and iStorage.
Perimeter Security
As threat vectors expand across connected environments, securing the enterprise perimeter remains a foundational priority. Bulwark’s focus on perimeter security includes advanced solutions that protect users, applications, and networks against evolving cyber threats. The portfolio covers network access control, workspace virtualization, multi-factor authentication, network monitoring, centralized alerts and notifications management, and threat exposure management.
With a broad portfolio in this domain, Bulwark enables a multi-layered security framework that strengthens visibility and resilience, across hybrid environments. The solutions in this segment are from leading vendors including ScopNet, Accops, SecureEnvoy, Motadata, SendQuick and CyberCyte.
Operational Security
As IT environments grow more distributed and complex, organizations are placing greater emphasis on operational resilience and workforce readiness to ensure uninterrupted performance. Bulwark’s IT operations and resilience portfolio integrates service desk management, IT asset tracking, secure remote access, data backup, and management tools with cybersecurity training and simulation platforms.
The focus is on strengthening operational visibility and responsiveness,
Feature by:
ensuring that IT teams can manage assets, secure data seamlessly across hybrid environments and support users. Bulwark has partnerships with Motadata ITSM, MSP360, NetSupport and Cyberbit for this segment.
Vulnerability Stack
Proactive vulnerability management has become essential to identifying and mitigating risks before they can be exploited. Bulwark’s vulnerability and assessment portfolio encompasses web vulnerability assessment, integrated vulnerability management across IT, OT, and IoT environments, storage and backup security configuration assessment, mobile application security, penetration testing, and adversary simulation solutions. Together, these capabilities enable organizations to identify, analyze, and mitigate security gaps before they can be exploited.
By combining automated assessments with adversary attack simulations, Bulwark helps enterprises strengthen their overall security posture and maintain continuous compliance across complex hybrid infrastructures. Bulwark has partnerships with Invicti, Mend.io, Continuity, Appknox, Core Impact and Cobalt Strike in this domain.
Endpoint Security
Endpoints remain the most targeted entry point for attackers. Bulwark’s endpoint and identity security portfolio covers endpoint detection and response (EDR), data loss prevention (DLP), privileged identity and access management, patch management, insider threat detection, smart ID, PKI, and single sign-on (SSO) solutions. It also includes enterprise mobility management and secure enterprise browser technologies that safeguard endpoints and users across devices and environments.
Together, these capabilities provide continuous monitoring, secure identity governance, and data protection, thus enabling enterprises to prevent breaches, ensure compliance, and maintain trusted access within hybrid work ecosystems. Bulwark partners with vendors including Eset, Digital Guardian, Safetica, Vicarius, Syteca, Nexus, 42Gears and Menlo Security to provide an extensive offering of endpoint solutions.
Built on Partnerships, Strengthened by Trust
For 25 years, Bulwark’s success has been defined by its ecosystem. Its long-standing relationships with global technology vendors have been built on mutual trust, collaboration, and shared innovation. These alliances allow Bulwark to adapt solutions to local markets and deliver truly end-to-end cybersecurity coverage.
With regional offices in the UAE, Saudi Arabia, and India, and a strong network of partners across the GCC and Africa, Bulwark continues to strengthen its ability to deliver localized expertise with global scale.
“We will further deepen our relationships with vendors and channel partners, fostering innovation and collaboration,” says Jose Menacherry, Co-Founder and Managing Director, Bulwark Technologies. “Our focus will always remain on providing niche solutions that empower businesses to operate securely and efficiently.”
Bulwark continues to invest in training, R&D, and channel enablement, ensuring its partners and customers remain equipped to address tomorrow’s threats today.
Today, as enterprises embrace pervasive digital transformation, the company stands ready to help them build security that moves at the speed of innovation where every risk is fixed faster and every layer is secured.
Zero Trust & Identity Security – Moving Beyond Traditional Security Paradigms
Instead of assuming that what’s inside the network is safe, Zero Trust continuously verifies every request, user, and device, regardless of location writes Murali Vellat,Division Manager, Bulwark Technologies

In today’s hyper-connected digital world, the conventional castle-and-moat approach to cybersecurity is rapidly losing relevance. Enterprises can no longer rely solely on strong perimeter defenses when users, applications, and data are scattered across cloud platforms, remote devices, and hybrid work environments. Threat actors have become more sophisticated, exploiting insider risks, stolen credentials, and lateral movement once inside networks. This shift underscores the need to move beyond traditional security paradigms and embrace Zero Trust coupled with robust Identity Security as the new foundation of enterprise defense.
Why Traditional Security Models Fall Short Historically, organizations placed trust in anyone or anything within the perimeter. Firewalls, intrusion prevention systems, and endpoint defenses created a layered defense meant to keep adversaries out. However, once an attacker gained access, they often enjoyed near-unrestricted movement within the environment.
• This perimeter-centric thinking has been rendered obsolete by:
• Remote workforces accessing corporate resources from outside traditional networks.
• Cloud adoption, where applications and work-
loads reside outside the datacenter.
• Proliferation of devices including IoT, mobile, and personal hardware.
• Identity-driven threats, where compromised usernames and passwords remain the leading cause of breaches.
The result: trust assumptions within the perimeter create blind spots that adversaries exploit.
Zero Trust – “Never Trust, Always Verify”
The Zero Trust model turns conventional thinking on its head. Instead of assuming that what’s inside the network is safe, Zero Trust continuously verifies every request, user, and device, regardless of location. Its core principles include:
1. Continuous verification – Authentication and authorization are not one-time events but ongoing processes.
2. Least privilege access – Users are given only the minimal rights necessary to perform tasks, reducing exposure.
3. Micro-segmentation – Workloads and data are isolated to prevent lateral movement.
4. Contextual policies – Access decisions consider user behavior, device posture, geolocation, and risk indicators.
Zero Trust recognizes that identity is the new perimeter. A secure enterprise is one that can validate who is accessing what, under which conditions, at all times.
The Central Role of Identity Security
While Zero Trust provides the strategic framework, Identity Security is the operational cornerstone. If identity is the new perimeter, securing it is non-negotiable. This involves:
• Strong authentication mechanisms such as multi-factor authentication (MFA) and passwordless access.
• Digital identity lifecycle management to ensure issuance, revocation, and governance of credentials remain tightly controlled.
• Certificate-based trust that ensures secure communications and device authentication.
• Compliance alignment to meet regulatory demands around data privacy and access governance.
By anchoring Zero Trust initiatives in strong identity frameworks, organizations can build resilience
against today’s most common attack vectors.
Beyond Security – Enabling Digital Trust
What’s often overlooked is that identity security is not just about reducing risk—it also creates opportunities. A workforce equipped with seamless, secure digital identities enjoys smoother access to resources, reduced login friction, and a consistent user experience across multiple platforms. Similarly, organizations interacting with customers, citizens, or partners can offer frictionless yet secure digital services.
The ability to issue and manage trusted identities—whether for employees, contractors, or devices—forms the backbone of modern digital ecosystems. It ensures not just security, but also credibility, trust, and compliance in a world where digital interactions dominate.
Moving Forward
Enterprises adopting Zero Trust and Identity Security must view it as a journey rather than a switch. The roadmap includes:
• Assessing the current state of identity and access management.
• Building a phased implementation plan aligned with business priorities.
• Leveraging standards-based solutions for interoperability and scalability.
• Partnering with trusted technology providers who specialize in digital identity, credentialing, and secure access infrastructures.
By taking this approach, organizations can safeguard critical assets, enable digital transformation, and maintain the trust of stakeholders.
Conclusion
The age of perimeter-based security is over. Today, the most valuable asset in the digital enterprise is identity, and the most effective defense is a Zero Trust strategy rooted in strong identity security. Organizations that embrace this paradigm shift not only reduce cyber risk but also unlock the potential of trusted digital interactions.
As enterprises modernize, partnering with experts in digital identity and credential management becomes essential. With the right foundation, Zero Trust and Identity Security can transform cybersecurity from a reactive defense into a proactive enabler of trust, resilience, and innovation.

What’s Appknox showcasing at Black Hat this year, and how does it reflect your evolution as a mobile AppSec leader?
At Black Hat this year, we are showcasing the full strength of our AI-powered mobile application security platform, with a spotlight on Storeknox, our newest capability for mobile app store monitoring and brand protection.
We have gone beyond traditional SAST, DAST, and API testing by adding privacy assessments and SDK risk analysis. Our mission has evolved from helping companies “fix bugs fast” to helping them build resilient mobile applications that stay secure across their lifecycle, even in the face of evolving AI-powered threats. Appknox leverages AI to make vulnerability assessment smarter - surfacing the most critical threats first and reducing noise for security teams
Saudi Arabia is making massive strides in digital innovation. How is the mobile threat landscape evolving there and how is Appknox adapting to meet regional needs?
The Kingdom is leading one of the most ambitious digital transformation journeys globally, from open banking to government super apps. As mobile becomes the default
AI-Powered Mobile Security to the Forefront
Subho Halder, CEO & Co-Founder, Appknox outlines the company’s latest innovations, its strategy for the Middle East, and the trends that will define the next era of mobile application security.
interface for citizens and customers, attackers are following close behind.
We are seeing a sharp rise in targeted threats, third-party SDK risks, and compliance pressures, especially as regulators like SAMA and NCA raise the bar.
At Appknox, we have responded by custombuilding for this market: offering local hosting, 24x7 support tailored to Gulf time zones, and automated compliance testing mapped to regional frameworks.
For security leaders in Saudi Arabia, this is the moment to shift from reactive fixes to proactive security, and we are here to help them lead that change.
There is growing interest in AppSec posture management and continuous testing. How is Appknox enabling security teams to shift from reactive to proactive?
We are seeing a clear shift in mindset - security teams do not want just another scanner; they want visibility, control, and automation.
With Appknox, teams can integrate AppSec testing directly into their CI/CD workflows, schedule automated scans, and get prioritized, developer-ready fixes, all in one platform.
Our platform also supports API testing, software bill of materials, and compliance reporting, making it easier to track posture and reduce risk before apps go live.
You have spoken about ‘AI fighting AI’ in cybersecurity. How is Appknox staying ahead in this invisible war?
We like to say: “Security for AI, and AI for
Security.” On the one hand, we have built AI/ ML models that help detect vulnerabilities in minutes, including AI-generated application flaws and phishing risks. On the other hand, we are scanning and analyzing AI-introduced vulnerabilities as developers increasingly use tools like Copilot or ChatGPT.
This dual focus allows us to catch what others might miss, whether it’s a hidden prompt injection vulnerability or unsafe API behavior baked into auto-generated code.
What excites you most about the future of mobile application security?
We are seeing mobile application security move from the fringes to the forefront. What was once a final-stage checklist item is now a board-level concern, especially as mobile becomes the default interface for banking, identity, and citizen services.
Gartner’s 2025 Hype Cycle for Application Security reflects this shift. Mobile app security is climbing the Slope of Enlightenment, as organizations seek more integrated, continuous, and AI-enabled solutions.
We are proud that Appknox is one of the vendors recognized in the report, and we believe our work in real-time risk detection, compliance mapping, and store-level monitoring is helping accelerate this maturity curve.
What excites me most is this: security is no longer just about blocking threats. It’s about enabling innovation - faster, safer, and with more trust.

















Jose Menacherry, MD
Bulwark Technologies shares the company’s vision and milestones during the Silver Jubilee celebrations.
Moe Bux, Channel Manager at Forta highlighted how Fortra is helping break the chain of data risk.
Werno Gevers, Regional Director at Mimecast spoke about email security threats and resilience strategies.
A keynote by Daniel McClean, Director of International Sales, DNSFilter highlighted cloud-based threat intelligence and secure browsing solutions.
Anoop Kumar Paudval, CISO at Gulf News presented a guest keynote.
ESET was awarded for its long-standing partnership with Bulwark - Hadi Anwar, CEO of CPX hands over the Award to Husni Hammoud, MD of Midis Group.
Bulwark & Mimecast teams at the silver jubilee celebrations, reinforcing their long-standing partnership.
Bulwark Saudi team with partners have together shown strong regional growth.
Delegates and guests at the event unite to celebrate Bulwark’s 25-year journey of trust and innovation.
Team Bulwark with some strategic partners, highlighting camaraderie that is the key to enduring alliances.
Bulwark–Accops partnership continues to enable trusted remote access and workspace security for enterprises.
Bulwark’s key partners from Oman also participated in the celebrations.
Bulwark & Fortra team have together focused on driving awareness about data protection and insider threat defense under the “Break the Chain” initiative.
Bulwark & DNSFilter team have been strengthening their partnership across the Middle East.
Bulwark management with Mr. Ramgopal, GM, Kanoo IT, celebrating a successful collaboration.
Bulwark with esteemed partnershonouring the ecosystem that powers cybersecurity success across the region.
Bulwark & ESET ‘s successful partnership continues to emphasize multi-layered endpoint and threat protection excellence.
Bulwark has always focused on building and celebrating its channel.
TESTIMONIALS FOR SILVER JUBILEE YEAR
“On behalf of everyone at iStorage, I extend our heartfelt congratulations to Bulwark on this significant occasion. Our enduring partnership has been a cornerstone of our mutual success and we deeply value the dedication and excellence that Bulwark brings to our collaboration. While we regret not being able to join you in person, please know that we are celebrating with you in spirit. Here’s to continued growth and shared achievements in the future.”
John Michael CEO, iStorage/Kangaru
“Congratulations on reaching this remarkable 25-year milestone! It’s truly inspiring to see your journey of growth, innovation, and strong partnerships over the years. Wishing you continued success, new achievements, and even greater impact in the years to come.”
Ahmad Halabi Managing Director, Resecurity
“Congratulations on reaching an incredible milestone your 25th anniversary! This remarkable journey stands as a testament to your commitment, resilience, and unwavering dedication to excellence.
We are truly honored to be recognized as your Best Enterprise Partner. Thank you for this meaningful award it is not only a privilege but a strong motivation for us to continue delivering value and growing alongside you.
Over the years, your partnership has been instrumental in building trust, achieving shared goals, and driving innovation. Here’s to celebrating your legacy and looking forward to many more successful years together!”
Rakesh
Agrawal General Manager, Seven Seas Technology
“I congratulate you and your team and Bulwark Distribution Company on your Silver Jubilee celebration.All the Best for the upcoming years and future business and relationships with the partners like us and others as well.”
Gyaneshwar
Mishra Head of Sales, Almoayed ICT, Bahrain
“We are truly honored to receive the Emerging Vendor Recognition award, and I extend my heartfelt gratitude to the entire team at Bulwark Technologies LLC for this recognition. Your unwavering support, trust, and belief in our vision have been instrumental in our growth across the Middle East.
At Motadata, we believe in building strong, strategic partnerships—and Bulwark has exemplified that spirit in every engagement. This award is not just a milestone; it’s a reminder of what we can achieve together.
We look forward to deepening our collaboration, unlocking new opportunities, and driving meaningful impact for customers across the region. The journey ahead is bright, and together, I am confident we will reach even greater heights.”
Amit Shingala CEO, Motadata
“Congratulations on your 25th Anniversary! As your partner, we’ve witnessed firsthand your unwavering commitment to quality and innovation. Your dedication has not only driven your success but has also been a significant value-add for us, enabling us to better serve our customers. We deeply appreciate your collaborative spirit and the trust you’ve placed in us. Here’s to many more years of mutual growth and success together!”
Rajesh
Koul Sales Director, Hilal Technologies, Bahrain
The Cyber Shift: Intelligence, AI, and the Cloud
Experts from Bulwark Technologies share their insights on key trends shaping the region, from threat intelligence and AI-powered SOC operations to the growing role of AI in marketing and the challenges of securing multi-cloud environments.
Cloud Security & Multi-Cloud Risk
The adoption of multi-cloud environments is rapidly increasing among businesses due to the greater flexibility, scalability, and cost-efficiency they offer compared to hybrid cloud solutions. A multi-cloud setup involves using services from multiple public cloud providers simultaneously. These environments can include public, private, or a combination of both types of clouds.
The primary objective of a multi-cloud strategy is to provide the flexibility to select the most suitable computing environment for each specific workload. However, this approach also presents several challenges, such as increased management complexity, maintaining consistent security, integrating diverse software environments, and ensuring reliable performance across multiple clouds.
Key pillars of cloud security include Identity and Access Management
(IAM), Encryption, Network Security, Compliance and Governance, and Incident Response and Recovery. Cloud Access Security Brokers (CASBs) play a vital role in securing cloud data. Acting as a gatekeeper between an organization’s on-premises infrastructure and the cloud, CASBs monitor and enforce security policies across all cloud applications and services. They provide organizations with enhanced visibility into cloud usage and help ensure compliance with regulatory requirements.
Encryption safeguards data at rest (when stored), in transit (when moving between locations), and sometimes in use, using cryptographic algorithms and keys. This process is a crucial component of overall cloud security, protecting sensitive information, intellectual property, and personal data from breaches and cyberattacks.
The broader goal of cloud security is to

Varkeychan Davis Technical Manager,Bulwark Technologies
block unauthorised access to data and resources, while safeguarding user accounts from compromise. By implementing CASB, encryption and other security technologies, organizations can effectively manage cloud-related risks, protect critical data, and maintain compliance with regulatory standards.

How AI is Reshaping Detection, Response, and SOC Operations
Artificial Intelligence is transforming how Security Operations Centers -SOCs detect and respond to threats. Traditional SOCs often struggle with a digital tsunami of alerts, delayed responses, and limited visibility. AI changes this by bringing automation, speed, and intelligence into the mix. With AI-driven analytics, organizations can detect anomalies in real time, correlate massive data sets, and prioritize
Threat Intelligence & Regional Threat Landscape
Threat Intelligence is the process of collecting, analyzing, and applying knowledge about current and emerging cyber threats to protect organizations effectively. It provides actionable insights that help security teams anticipate, prevent, and respond to attacks. A strong threat intelligence program enables proactive defense rather than reactive measures.
The regional threat landscape reflects unique risks shaped by geography,

politics, and digital adoption. In the Middle East, critical sectors such as energy, finance, and government face sophisticated attacks, often driven by state-sponsored actors and organized cybercrime. Phishing, ransomware, and supply chain compromises remain prevalent. By integrating global intelligence with localized context, organizations gain deeper visibility, enhance resilience, and ensure that security strategies align with evolving regional challenges.
alerts based on true risk. Machine learning continuously adapts from past incidents, improving accuracy and reducing false positives. AI-powered response playbooks enable faster containment, minimizing damage. As cyber threats grow more sophisticated, AI empowers SOCs to shift from reactive firefighting to proactive defense — making security smarter, faster, and more resilient than ever.

Influence of AI on Marketing
Artificial Intelligence (AI) is revolutionizing marketing by enabling businesses to deliver highly personalized experiences, optimize campaigns, and predict consumer behavior with greater accuracy. AI-driven tools analyze data to identify trends, segment audiences and automate content creation. Chatbots enhance customer service, while recommendation engines boost engagement and sales. Predictive analytics allow marketers to anticipate needs and tailor messages in real time. Additionally, AI streamlines ad targeting, reducing costs and improving ROI. As AI continues to evolve, it empowers marketers to make data-informed decisions, fostering deeper customer relationships and driving business
growth through smarter, more efficient marketing strategies.
Artificial Intelligence is a game-changer in the world of marketing. AI is completely transforming how brands connect with their audiences.
Every click, search, or purchase tells a story. Marketers can now deliver hyper-personalized campaigns, anticipate customer needs, and make smarter decisions efficiently.
AI doesn’t replace marketers, it empowers them. The future of marketing isn’t about selling harder; it’s about connecting smarter.
Ibrahim Shaban Country Head KSA – Bulwark Saudi for Information Technology
Sonali Basu Roy Marketing Manager,Bulwark Technologies
Don Joy Group Product Manager,Bulwark Technologies
The Shield Crossword Challenge
Flip through this magazine, fill out the crossword, and you could win an Apple iPad!
Theme: Cybersecurity Crossword Level: Easy
Bonus: Find all answers inside this issue of The Shield

ACROSS
1. UAE framework Fortra references among MEA regulations
3. Portfolio focused on breaking the attack chain across stages
5. AppSec platform that embeds checks in IDE/PR & CI/CD
9. The practice of preventing sensitive data from being shared outside
10.Enterprise messaging brand offering MFA & incident alerts
DOWN
2. Appknox’s new tool for monitoring app stores
4. Invicti’s platform that manages and prioritizes application security findings
6. Type of security testing Invicti use to find vulnerabilities at runtime
7. Runtime web app scanning brand with proof-based results
8. Type of authentication, supported by SendQuick Conexa, does not require a password
Instructions & Rules
• All questions are based on the content of this magazine.
• Only one entry per person is allowed.
• Entries close on 31st October 2025
• Prize - One winner will receive an Apple iPad -11inch.
• Winners will be chosen through a lucky draw from all correct entries.
• Winners will be announced via Bulwark’s official social media pages — follow us to stay updated!
• Please scan the QR Code to submit the completed crossword
• Reach out to info@bulwark.biz if you have any questions
• The decision of the editorial team will be final.



Hall 25, Stand No: D-50
The Worldʼs Largest Tech, AI & StartUp Show

13-17 October 2025
Dubai World Trade Centre


Riyadh Exhibition & Convention Centre, Malham, KSA Meet us at Dubai World Trade Centre

2-4 December 2025

Hall:1, Stand : V110